Building Your Cybersecurity Brick House
By Barry Semple
Director of Technology
When you work in IT, you get asked about cybersecurity a lot. But it’s always very specific questions and rarely about the complete picture. And believe me, it’s a big picture.
People wonder about anti-virus or sometimes ask about ransomware because they’ve heard it on the news. But most don’t have any idea how complex an issue cybersecurity really is. And that often means that even businesses aren’t aware of everything they need to address to ensure proper data security.
To get the point across, I often describe cybersecurity like a brick building - that requires layer upon layer of structure to build strength. Without all the layers and bricks cemented into that structure – there are weaknesses. And those weaknesses indicate vulnerabilities that can be exploited.
The Layers – Building Your Cybersecurity Foundation
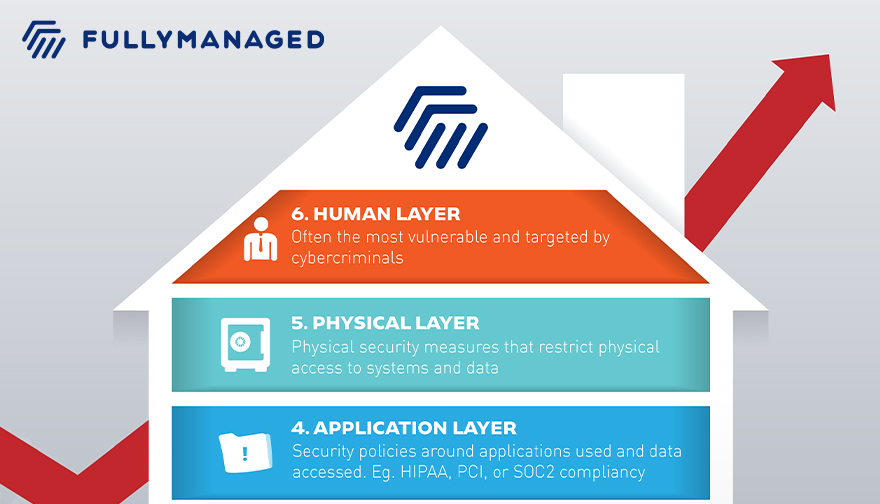
So what are the security layers that organizations need to consider in a comprehensive cybersecurity strategy?
- End point layer (Antivirus/Malware Protection for devices accessing data)
- Network layer (Network traffic & activity monitoring)
- Perimeter layer (Firewalls & other security tools block outside access)
- Application layer (Security policies around applications used and data accessed – for eg. HIPAA, PCI, or SOC2 compliancy)
- Physical layer (Physical security measures that restrict physical access to systems and data)
- Human layer (Often the most vulnerable and targeted by cybercriminals)
Security First! A Few Additional Points
As we’ve just mentioned, the human layer is of particular importance. End users, that means you and I, are the biggest targets for cyber attacks. People are curious, we often click on things before thinking about them and the cyber thugs out there know it. Regular training is vitally important for everyone on your team. Security isn’t just an IT responsibility – it belongs to everyone, a shared responsibility.
The Internet of Things (IoT) is also a concern and something that needs to be addressed in security policy and planning. IoT refers to devices, sensors, wearables – anything connected to the network that gathers or inputs data. Now don’t get me wrong – IoT is the way of the future – automation through connected devices is incredibly helpful. But those devices can also be a gateway for cybercrime.
So when your organization is considering its technology strategy, make sure security planning is front and center. Your data is of critical importance to operations and in some cases subject to strict regulations and compliance standards. Build that layered foundation through planning, policy documentation, and action.
Security first!
Read more in this Series: